Password Requirements, They Are A-Changing!


Password Requirements, They Are A-Changing!
By Cindy Murphy, M.Sc., President of Gillware Digital Forensics
 Passwords. We all understand why they’re needed, and we know the general rules about length and complexity and guess-ability. But let’s face it – passwords are a pain. Remembering and changing passwords has been a long-time annoyance for most computer users. And weak or easily guessable passwords are a definite security problem.
Passwords. We all understand why they’re needed, and we know the general rules about length and complexity and guess-ability. But let’s face it – passwords are a pain. Remembering and changing passwords has been a long-time annoyance for most computer users. And weak or easily guessable passwords are a definite security problem.
In addition, re-using passwords across multiple sites and accounts can cause a minor-seeming account hack to snowball out of control—once a hacker gets into one account, they have the proverbial keys to the kingdom, as it were, and have total access to any other account of yours that shares the same password.
As cryptographer and computer security expert Bruce Scheiner puts it, “The whole notion of passwords is based on an oxymoron. The idea is to have a random string that is easy to remember. Unfortunately, if it’s easy to remember, it’s something nonrandom like ‘Susan.’ And if it’s random, like ‘r7U2*Qnp,’ then it’s not easy to remember.”
The truth is that, unfortunately, a clear majority of people don’t follow the general rules—mainly because following them and satisfying the demands of the ravenous password god is a huge pain in the rear! After all, how can all of your passwords be unique, memorable, and complex enough to stymie a supercomputer?
Instead, many people end up relying on passwords that are easy to remember and easy to guess. What’s worse, they reuse passwords across multiple accounts and hope that they never get caught or compromised. And when we’re forced to change passwords by well-meaning IT Admins, most of us change our current passwords only slightly so we don’t forget them and get locked out.
It’s Time for a Change in Password Requirements
Don’t despair, though—We have some great news for those of you who don’t like the current state of passwords! The National Institute for Standards in Technology (NIST) is revamping its recommendations on passwords in 800-63-3: Digital Identity Guidelines, their first major update of password advice since 2003. And for once, things are going to get easier for real people, while at the same time making it harder for cyber-criminals to compromise accounts.
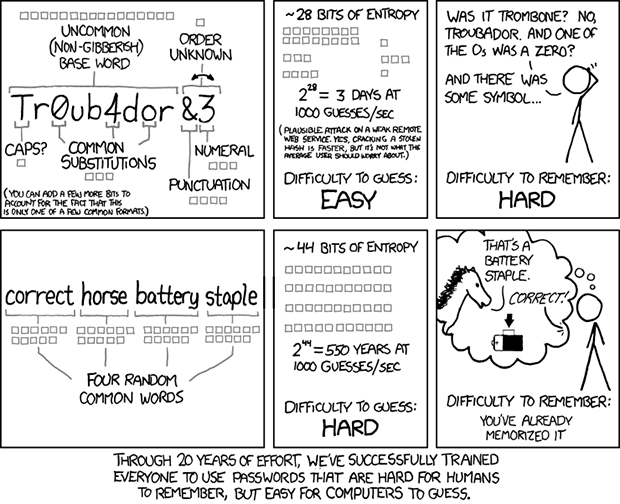
The new NIST password recommendations include some common sense advise like using pass phrases such as four easy to remember random words rather than trying to build algorithmic complexity into passwords by using arbitrary combinations of upper case letters, symbols and numbers. This has been shown to result in weaker passwords, as Randall Munroe’s often-passed-around XKCD comic strip demonstrates.
It’s easier to remember these random words, since your brain is typically much better at finding patterns between seemingly-unconnected words than random alphanumeric strings, aiding in recall. And when passwords start piling up (especially if you’re trying to keep up with the ever-splintering world of online streaming media), you can always use a secure password manager app to store them and aid in your recollection. Password managers are becoming so commonplace that the technicians at Gillware’s data recovery lab always make sure to search for password database files when salvaging data for customers.
Requirements for periodic password changes are also being removed from the NIST recommendations, which will result in lots of celebration. Requiring frequent changes of passwords can actually be counterproductive, as people replace strong passwords with weak passwords out of frustration, or weak passwords with even weaker passwords. The truth is, a truly strong password doesn’t need to be changed unless you have good reason to believe it’s been compromised.
So what does NIST recommend for modern passwords?
In short, the NIST recommends longer but less complex passwords. The NIST guidelines say that length is key to password strength. A password or passphrase of 8 to 64 characters is sufficient to keep your data safe, as passwords require exponentially more computer time for a would-be hacker to “guess” as their length increases.
The NIST also recommends that certain passwords should be prohibited, including passwords known to have been previously stolen, passwords with repetitive or sequential characters, or passwords using simple dictionary words. It’s long been time to issue a moratorium on these types of passwords. That’s right—no more using “Password” for your online bank account, or “12345” for your luggage.
Also struck out are passwords that contain the user’s name, the name of the service, or other account-related or otherwise personally-identifiable information. Using such common words lets hackers drastically reduce the amount of time it takes to try and crack a password, as they can simply use information they know about you (from stalking you on social media or just looking you up) to make much more educated guesses about your password.
NIST says that any ASCII or Unicode characters should be allowed in passwords, but are not necessarily required. They also recommend that you only change your passwords after a security breach.
These commonsense recommendations result in a wider universe of passwords that are both easy to think up and to remember and still hard for others to guess and computers to crack. Combine this new password production paradigm with password management software and enable two-factor authentication on your accounts, and you’ll make all your password-related woes a thing of the past.