Accidental Leaking of Attorney/Client Information – Metadata “Gotchas”
Accidental Leaking of Attorney/Client Information – Metadata “Gotchas”
This article was written by Cindy Murphy, M.Sc., President of Gillware Digital Forensics. With 17+ years of digital forensics experience, Cindy oversees each digital forensics case brought to Gillware.
I recently did a very grown up thing. I hired an attorney to prepare my estate planning documents, including a simple will, power of attorney documents, and that sort of thing. There were 7 documents in all, and because of my life’s circumstances, all of them were fairly straight forward and non-complex.
When the attorney sent me the documents for review, I found some minor typos and misspellings. But I also found something much more concerning – the name of a previous client within the content of one document, and the address of another client within the content of a second document.
I was told by the mortified attorney that these were find-and-replace errors by his assistant. He apologized and quickly offered to remedy the problem.
As a digital forensic examiner for over 20 years, this caused me to dig deeper, and to look at the metadata of the documents. This might seem like a complex task, but in this case, it’s as easy as looking at a document’s properties.
What I found was concerning. Every single one of the 7 documents had information leakage with client data within the metadata. I then had a tough conversation with the attorney to clarify the larger problem: the document creation process in his office was leading to unnecessary mistakes and worse, confidential client data being leaked to his other clients, and there was no protocol to catch and remedy the problem.
What Is Metadata?
 Let’s talk about “metadata.” Metadata is simply data about data. Metadata information is embedded within all kinds of electronic files stored in the cloud, on cell phones, and in computer hard drives, and it can help to tell the story of that data’s ‘life’. In digital forensics and e-discovery, we commonly use metadata in our investigations to answer questions, and to identify discoverable data and the origins of documents.
Let’s talk about “metadata.” Metadata is simply data about data. Metadata information is embedded within all kinds of electronic files stored in the cloud, on cell phones, and in computer hard drives, and it can help to tell the story of that data’s ‘life’. In digital forensics and e-discovery, we commonly use metadata in our investigations to answer questions, and to identify discoverable data and the origins of documents.
There are different sorts of metadata for different kinds of data, but suffice it to say, metadata can reveal a huge amount of information about a file. For instance, metadata for a .jpg image file (also known as “EXIF” data), can contain dozens of bits of information known as metadata tags that contain the camera make and model, flash settings, orientation and focal point information, not to mention GPS coordinates. Most users are still unaware of the vast amount of information collected when they take even a single digital picture.
“Gotchas” and How They Happen
How did this happen? This was a case of a previous client’s documents being used as templates for the creation of my estate planning documents.
The assistant, who was unaware of metadata from the previous document carrying over to the new document neglected to check it or to change it, and client’s names were used in the file name and descriptions of the documents. The typos, misspellings, address and client name in the content of the document itself were simply human error.
 Avoiding Sensitive Metadata Leaks
Avoiding Sensitive Metadata Leaks
A simple way to avoid this problem is to work from clean document templates and use the “Save As” feature rather than “Save” feature. Each newly created document then has its own unique metadata created and associated with it.
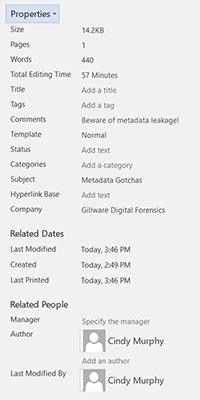
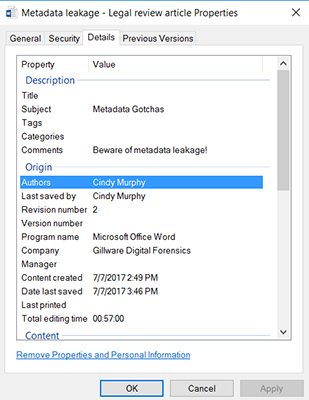
File metadata can be reviewed by right clicking on a file, choosing to view its properties, and then selecting the “details” tab, or through the File menu in the Info tab. Both choices provide options for inspecting the document and removing or changing information and properties.
As you can clearly see, metadata for a Word Document potentially contains information that is useful for determining the original source and author of a document, when it was created, how long the document was being edited, and whether and when the document was last printed.
If you aren’t aware that this information is being collected and stored, however, there is the potential to unintentionally leak client information. Setting proper processes and protocols to prevent data leakage could save you a lot worse than embarrassment in the future.
–
Gillware Digital Forensics and Gillware Electronic Discovery offer digital forensics and eDiscovery services, including ESI collection and analysis. If you are in need of these services, our digital forensics lab in Madison, Wisconsin is more than happy to assist you.







